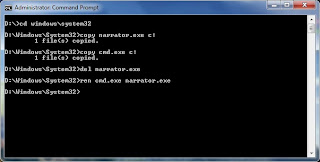
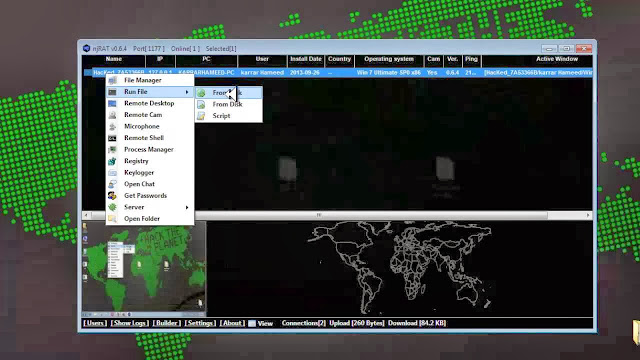
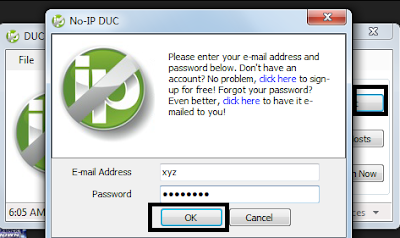
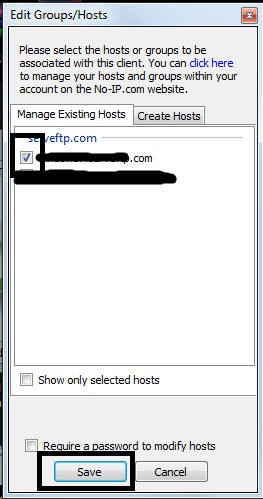
Have you ever re-installed Windows again just because you forgot your
Administrator Account password? Well you don't need to do that again,
using this simple trick you can easily get into your Administrator
Account and reset your password.
This trick can be used to hack ANY PC or Laptop, no matter what version of Windows are you using, you just need to know how to access the boot-menu and *Boom*.

I know there are also some other methods to do this job, but i believe that this is the easiest trick for a normal user without any technical knowledge of computers.
So before you continue reading, i want you to know that this tutorial is for educational purpose only, please DON’T use it to harm anyone.
This trick can be used to hack ANY PC or Laptop, no matter what version of Windows are you using, you just need to know how to access the boot-menu and *Boom*.
I know there are also some other methods to do this job, but i believe that this is the easiest trick for a normal user without any technical knowledge of computers.
So before you continue reading, i want you to know that this tutorial is for educational purpose only, please DON’T use it to harm anyone.
Things you need:
- A USB Pen-drive (Memory Card can also be used, as Computer recognizes it as a USB device)
- KON-Boot
Step 1:
Download this little tool called KON-Boot from here and Extract it using WinRAR.Also Read Hack Windows XP/7/8 admin password easily without any software
Step 2:
Connect the USB and Format it.Step 3:
Now go to the extracted KON-Boot folder and run “unetbootin-windows-323.exe”Step 4:
Select Discimage option, and Browse to the same extracted files and select “D0-konboot-v1.1-2in1.img” file.Step 5:
In the bottom section of the window, choose the Drive Name (letter) of your USB Pen-drive, click Ok and wait for the process to complete.This will install KON-Boot on your USB drive.
The Drive letter might be J: , K: or any other alphabet, depending on the number of partitions, DVD Drives and Other connected memory devices on your computer.
Step 6:
Now the best part :) Plug the USB into the PC you want to access, go to the BIOS settings and choose USB Flash Drive as the primary boot device.e.g. In DELL you can simply press F9 while booting and select the USB FLASH DRIVE as boot device.
Also Read Hack Windows XP/7/8 admin password easily without any software
Step 7:
When the PC boots from the USB device you’ll see the KON-Boot screen and the Windows will get started normally.Step 8:
When the login screen comes up, just leave the password empty and hit Enter!! You’ll be logged into the administrator account without entering any password. :)Leave comments below if you have any questions or need any help.